In my current studies, I did some work about security inside networking data paths. In my recent work, I tried to get some experiments done that needed to use source based routing in order to be completed. Like most of the scientific work that tries to get from paper to experiment and then to something useful, it failed at the very beginning. If I can be more precise and improve a bit the appearance of my failure here. I can do it by explaining what happened and what did I came across while researching my idea. It’s something as simple as this:
Table of Contents
Source based routing, by the suggestion of IETF needs to be disabled by default on networking devices. At least it should be as the feature itself is recognised as a major security threat and IETF itself is trying to get rid of it.
Of course that can be considered like a stop sign in an experiment where you are relying solely on source based routing to get your thing running. (:
When you look at the networking technology these days that’s probably IP protocol that you are talking about. Okay maybe you are new age junkie and you are probably speaking about IPv6 protocol. Either way, the very first and main principle of routing packet across data network is based on the destination IP address routing/decision making. Router is making decision on where will he send some packet based more or less solely on destination IP address. It is doing so by reading his locally built routing table of destination subnets. From that table router gets the info out of which interface will he sent the packet that is destined for some address.
When the whole architecture and the logic behind routing was developed the idea was all about getting the packet to the destination by the best path possible. Based on the routing table build from the info received from their neighbors, routers will be able to calculate best path to destination subnet. But what if we want to force the packets to go across some other way. What if we want the packet to visit some other destinations before being routed to final destination written inside his destination address IP header? It was made possible.
In either IPv4 and IPv6 protocol there is a built-in option for a sender device to force the path for packets that are being sent. The mean of the sender to influence and change normal best path routing implemented by every routing protocol is called source routing.
I want to be clear here, you have all sorts of traffic engineering out there that give you different way to control traffic paths that some datagram will be sent across. Almost all of those methods consider that you will need access to some routers along the way and change routing decision on them. This is of course not scalable for everyday use, particularly not if you are not the owner of those routers. If we speak about Internet here, and we are, then you are surely not he owner of those routers.
Source routing on other hand is basically on of those methods where you can influence routing and stay at home. In this case you do not need to get the access to other routers on the network except the first one that is sending the packet. You are able to get packet steered to some different path somewhere when they leave your source router without changing anything along the way. But how is that possible?
You are simply sending packets that already have all the waypoints that they needs to visit along the way written inside their headers. In the form of IP address of course.
There nothing so clear like a real example!
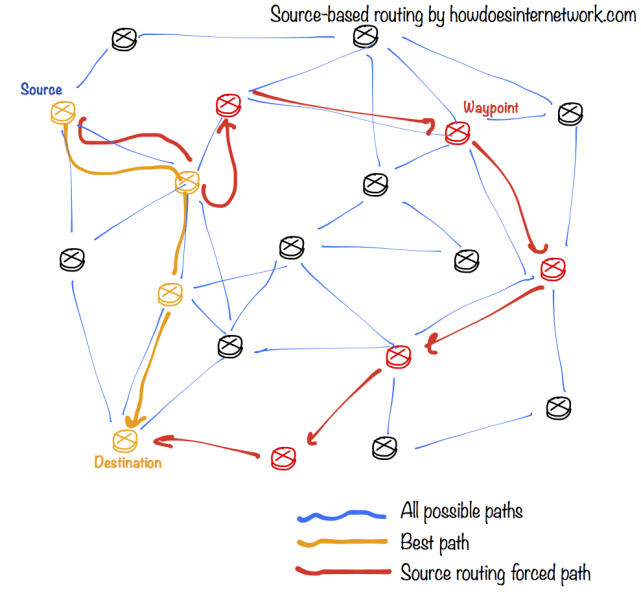
Packet usually follows normal routing protocol calculated path from source towards destination IP address. On the image above I draw that path in orange. Inserting source routing extension inside sent packets forces the packets to turn from second orange router towards waypoint IP address. Source routing extensions are simply in form of IP address of intermediary router/waypoint address. The waypoint router is one of the red routers with label “waypoint” on it of course. The thing is that when inserting source routing waypoint ip addresses inside the packet, packet is basically using destination routing again but this time only towards waypoint IP address. When it arrives to waypoint IP address device it will be the router with normal routing path again towards his real destination. It’s like saying to a packet: “Go to waypoint!” (he is your first destination) and then “Go to real destination”.
You can define more waypoints on the way to the destination. Including more waypoint routers make you get even more control on path choice and provides more discovery capabilities. Here somewhere was one of my PhD experiment basis and it surely fall apart after reading IETF suggestions on deprecating this way of doing things.
When we speak about IPv4 there are Loose and Strict Source Routing options – LSSR and SSR. When we look inside IPv6 world there is Type 0 Routing Header extension – RH0.
- IPv4
- LSSR – Lose Source Routing options
- SSR – Strict Source Routing options
- IPv6
- RH0 – Type 0 Routing Header extension
IPv4 networks are now safe because almost all network administrators listen to the suggestion of IETF and other security folks and in order to prevent security issues source routing options on routers are almost always disabled. After a while it resulted in that most vendor default configuration for devices is disabled source routing al least on router devices.
When we speak about IPv6 negative security impact regarding source routing enabled by Type 0 Routing Header is even worst than in IPv4. This resulted in IETF tries to completely deprecate the Type 0 Routing Header. It will basically means that the source routing in IPv6 protocol is completely kicked out of RFC.
Why?
Possible attack using source routing can have various forms, some of them include network discovery and denial-of-service attacks. DoS attack is one of the main reason for the deprecation suggestions.
Different implementation of source routing in IPv4 vs IPv6
IPv4 mechanism of source routing is enabled by adding the waypoint addresses inside option part of a header. Size of addresses list is limited in size and can be up to 40 bytes long. The reason for that is not security but simply the standard for IPv4 that defines option part of header not to be greater than 40 bytes. It’s good because it lets us make a list of 9 waypoint address at most.
IPv6 is a bit different of course. Source routing here is implemented in an extension header that is found after IPv6 header and before the upper-layer payload. Extension headers are different than normal option headers and they are not limited in size. They are taking the payload space to get more room when needed and thus they can become huge. If we do not permit the fragmentation in this experiment number of waypoint addresses in IPv6 extension header will be limited by the maximum size of the packet. Maximum size of the packet is defined by TCP MTU and in this case we can make a list of 90 waypoints inside the packet. This will be true if we assume the MTU of maximum 1500 bytes.
You can probably see that from security perspective IPv6 source routing is far worst that IPv4 implementation of the same thing. IT sounds great to be able and send the packet to 90 destinations before getting it to the last real destination address. But let’s take an example like this into account:
You send out some traffic at high-speed connection and tell to all those packets to visit this list of 90 waypoints on the way toward the end of the path:
- 2001:123:123::2
- 2001:123:123::3
- 2001:123:123::2
- 2001:123:123::3
- 2001:123:123::2
- 2001:123:123::3
- 2001:123:123::2
- 2001:123:123::3
- 2001:123:123::2
- 2001:123:123::3
- 2001:123:123::2
- 2001:123:123::3
- 2001:123:123::2
- 2001:123:123::3
- …
- …
- 2001:123:123::2
- 2001:123:123::3
If we know that those two address are existing on some devices on IPv6 internet that it is clear that we will get the bast route between them full of our junk traffic. They will start to forward our packets to each other until they do maybe 45 sends each, maybe 44 sends each and in that way probably congest the link. Imagine if they have 1Gb between them and I send 1GB of data all with that IPv6 extension headers. Do you see the issue here?
Basically, an attacker with only few Mbit/s upload link can congest more than 100 Mbit/s link without any problem.
Who is not doing RH0?
There were more different conferences and public speeches and also the IETF made considerable effort to stop the usage of RH0 inside routers and operating systems. Linux kernel 2.6.20.9 and later, most BSD versions, Apple after 10.4.10 are some vendors that did disable the RH0 couple of years ago. I am sure for Cisco that it is forwarding packet based on RH0 header by default and I thing Juniper is also one of those who did not change the default configuration.
On cisco devices you can easily turn RH0 off by typing:
(conf)#no ip source-route
Conclusion and reading suggestions
There are more attacks possible using source routing but for now I will stop here and perhaps write another article solely about those different attacks techniques. For now here’s the list of suggested articles about source routing that I stumbled upon during my research.